A Comprehensive Guide to 23 OSINT Tools for Cybersecurity Enthusiasts
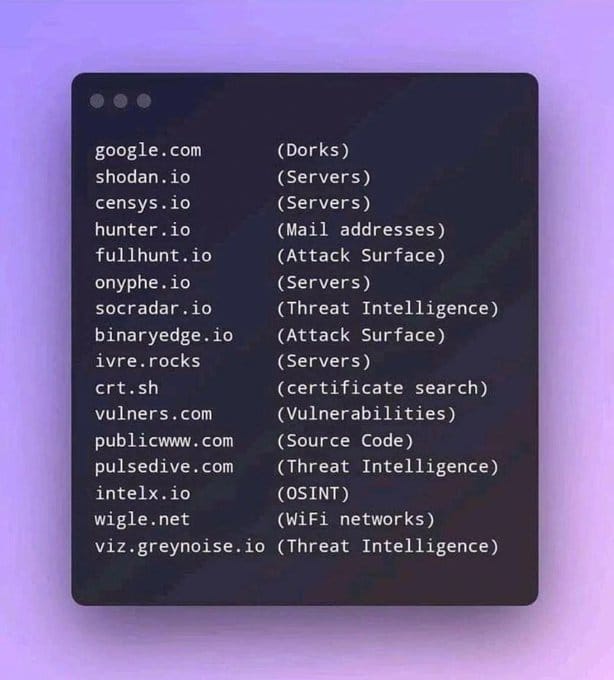
Introduction
Open Source Intelligence (OSINT) tools are invaluable for cybersecurity professionals and enthusiasts alike. These tools allow users to gather data from publicly available sources to understand, monitor, and protect against potential threats. In this article, we'll delve into some of the most popular OSINT tools listed in your image, explaining their use cases, features, and how they can be applied in real-world scenarios.
1. Google.com (Dorks)
Purpose: Google Dorks involve using advanced search operators on Google to find hidden information such as files, usernames, or passwords that are publicly accessible but not intended for public use.
Usage: Google Dorks can be used to uncover unsecured web servers, publicly exposed documents, or other sensitive data inadvertently made available online.
Tip: Always use Google Dorks responsibly, as exploring these resources can unintentionally breach privacy policies.
2. Shodan.io (Servers)
Purpose: Shodan is a search engine for Internet-connected devices. It can identify devices ranging from routers and webcams to servers and industrial control systems.
Usage: Security professionals use Shodan to assess the security posture of devices, look for vulnerabilities, and understand the exposure of assets on the internet.
Tip: Use Shodan’s filters to narrow down your searches, such as by country, port, or software.
3. Censys.io (Servers)
Purpose: Censys is another search engine for internet-connected devices that maps out the global internet to reveal devices, websites, and their underlying software.
Usage: It helps in identifying vulnerabilities, tracking down misconfigurations, and monitoring network assets.
Tip: Utilize Censys’s API to automate searches and integrate findings into your cybersecurity workflows.
4. Hunter.io (Mail Addresses)
Purpose: Hunter.io is used to find email addresses associated with specific domains, making it a valuable tool for penetration testing and reconnaissance.
Usage: Use Hunter.io to discover email formats and addresses, helping in crafting targeted phishing simulations or conducting OSINT investigations.
Tip: Cross-reference Hunter.io results with other sources to validate email addresses.
5. Fullhunt.io (Attack Surface)
Purpose: Fullhunt provides attack surface management by identifying and cataloging an organization’s assets exposed on the internet.
Usage: It is used to discover unknown assets, detect misconfigurations, and provide actionable insights to reduce attack surfaces.
Tip: Regularly monitor your attack surface with Fullhunt to keep up with changes and new exposures.
6. Onyphe.io (Servers)
Purpose: Onyphe aggregates data from the internet, darknet, and other OSINT sources to provide comprehensive cyber threat intelligence.
Usage: It is used for vulnerability assessments, threat hunting, and incident response.
Tip: Use Onyphe’s advanced filters to refine your search and get precise data relevant to your needs.
7. Socradar.io (Threat Intelligence)
Purpose: Socradar provides actionable threat intelligence and helps organizations detect cyber threats in real time.
Usage: It monitors the dark web, deep web, and other sources for potential threats targeting your organization.
Tip: Use Socradar’s threat feeds to stay ahead of emerging threats specific to your industry.
8. Binaryedge.io (Attack Surface)
Purpose: BinaryEdge scans the internet for exposed and vulnerable assets, offering insights into the attack surface of an organization.
Usage: It helps in identifying open ports, vulnerabilities, and publicly exposed services.
Tip: Incorporate BinaryEdge into your continuous monitoring process to maintain a secure perimeter.
9. Ivre.rocks (Servers)
Purpose: Ivre (IVRE stands for Instrument de Veille sur les Réseaux Extérieurs) is an open-source framework for network recon that provides insights into the internet-facing infrastructure.
Usage: It helps in network mapping and identifying accessible systems on the internet.
Tip: Use Ivre with other tools like Shodan for a more comprehensive analysis.
10. Crt.sh (Certificate Search)
Purpose: Crt.sh is an online tool for searching Certificate Transparency logs, which can be used to identify SSL/TLS certificates associated with domains.
Usage: It's useful for finding certificates that may have been issued fraudulently or uncovering new subdomains.
Tip: Regularly monitor Crt.sh to detect unauthorized certificates that could indicate domain spoofing.
11. Vulners.com (Vulnerabilities)
Purpose: Vulners is a search engine for vulnerabilities that aggregates information from multiple sources, including exploit databases, security bulletins, and blogs.
Usage: Use Vulners to stay up-to-date on the latest vulnerabilities that could affect your systems.
Tip: Integrate Vulners API with your security tools to automate vulnerability management.
12. Publicwww.com (Source Code)
Purpose: PublicWWW is a search engine for source code that allows you to find web pages containing specific code snippets, analytics, or widgets.
Usage: It can be used to identify websites using outdated or vulnerable JavaScript libraries, widgets, or content management systems.
Tip: Use precise queries to avoid overwhelming results, especially when searching for common code snippets.
13. Pulsedive.com (Threat Intelligence)
Purpose: Pulsedive provides threat intelligence through crowdsourced data, helping identify malicious domains, IP addresses, and URLs.
Usage: Use it for threat hunting, incident response, and to enrich threat intelligence databases.
Tip: Leverage Pulsedive’s community input to validate findings and get broader insights.
14. Intelx.io (OSINT)
Purpose: IntelX is an advanced search engine for OSINT that allows users to search across a variety of data sources, including leaks, breaches, and public data repositories.
Usage: It’s used for in-depth investigations, especially when tracing data leaks and breaches.
Tip: Combine IntelX searches with other tools for a deeper investigation into data breaches.
15. Wigle.net (WiFi Networks)
Purpose: Wigle is a global database of wireless networks that maps WiFi access points worldwide.
Usage: It’s often used in network mapping and security audits to identify rogue access points or poorly secured networks.
Tip: Be mindful of privacy and legal implications when using WiFi data from Wigle.
16. Viz.greynoise.io (Threat Intelligence)
Purpose: GreyNoise helps security professionals understand the nature of internet noise by filtering out background noise and focusing on relevant threat intelligence.
Usage: It is used to reduce false positives in security alerts and understand which threats are worth investigating.
Tip: Use GreyNoise to complement your existing threat intelligence feeds for a clearer threat landscape.
17. Spyse.com (Infrastructure Mapping)
Purpose: Spyse is a powerful search engine designed for cybersecurity professionals to gather and analyze data related to internet infrastructure, such as domains, IPs, ASNs, and SSL certificates.
Usage: It’s used for reconnaissance during penetration testing, threat hunting, and vulnerability assessment by providing a comprehensive view of the attack surface.
Tip: Utilize Spyse’s API for automated data gathering and integration with other security tools.
18. Maltego.com (Graphical Link Analysis)
Purpose: Maltego is an OSINT and forensics tool that provides graphical link analysis between people, groups, websites, and other entities, helping to visualize relationships in complex data sets.
Usage: It’s commonly used in threat intelligence, digital forensics, and investigations to map out networks of relationships.
Tip: Use Maltego’s transforms to integrate data from other OSINT tools and databases for more comprehensive investigations.
19. DNSDumpster (Domain Reconnaissance)
Purpose: DNSDumpster is an open-source DNS recon and research tool that helps in finding DNS records and mapping out domains.
Usage: It is used for gathering subdomains, email addresses, and DNS configurations associated with a target domain.
Tip: Use DNSDumpster in the initial phase of penetration testing or vulnerability assessment to map out the attack surface of a domain.
20. BreachDirectory.com (Data Breach Lookup)
Purpose: BreachDirectory allows users to search through databases of breached credentials, helping to determine if an email address or username has been compromised.
Usage: It’s useful for security professionals to monitor if any credentials related to their organization have been exposed in past breaches.
Tip: Regularly check your organization's domain to identify and mitigate the impact of leaked credentials.
21. Dehashed.com (Data Breach Search Engine)
Purpose: Dehashed is a search engine for finding leaked data, such as usernames, passwords, emails, addresses, and more, across multiple breaches.
Usage: It’s used to search for personal or organizational data that might have been compromised and leaked online.
Tip: Monitor your email addresses and other sensitive information regularly to ensure they have not been exposed in new breaches.
22. Recon-ng (Recon Framework)
Purpose: Recon-ng is a full-featured reconnaissance framework written in Python. It’s designed to help with data collection, analysis, and even exploitation of vulnerabilities.
Usage: It can gather information from various sources, including search engines, APIs, and social media, making it a versatile tool for OSINT investigations.
Tip: Recon-ng has a modular design, allowing users to add custom modules for specific tasks, making it highly adaptable to various reconnaissance needs.
23. SpiderFoot (Automated OSINT)
Purpose: SpiderFoot automates the process of gathering intelligence about IP addresses, domain names, emails, names, and other metadata across more than 100 public data sources.
Usage: It is widely used for scanning networks, discovering links between entities, and mapping out an organization’s internet footprint.
Tip: Use SpiderFoot’s built-in threat intelligence feeds to enrich your findings and better understand the context of the data collected.
Conclusion
These OSINT tools are powerful resources for anyone in cybersecurity, providing critical insights and enhancing the ability to proactively protect against threats. By understanding the capabilities and applications of each tool, you can better utilize them to strengthen your organization’s security posture. Remember to use these tools responsibly and within the bounds of legal and ethical guidelines.
For more detailed guides and tips on using these tools, visit HackerNoob Tips.





