A Comprehensive Guide to Using Nmap
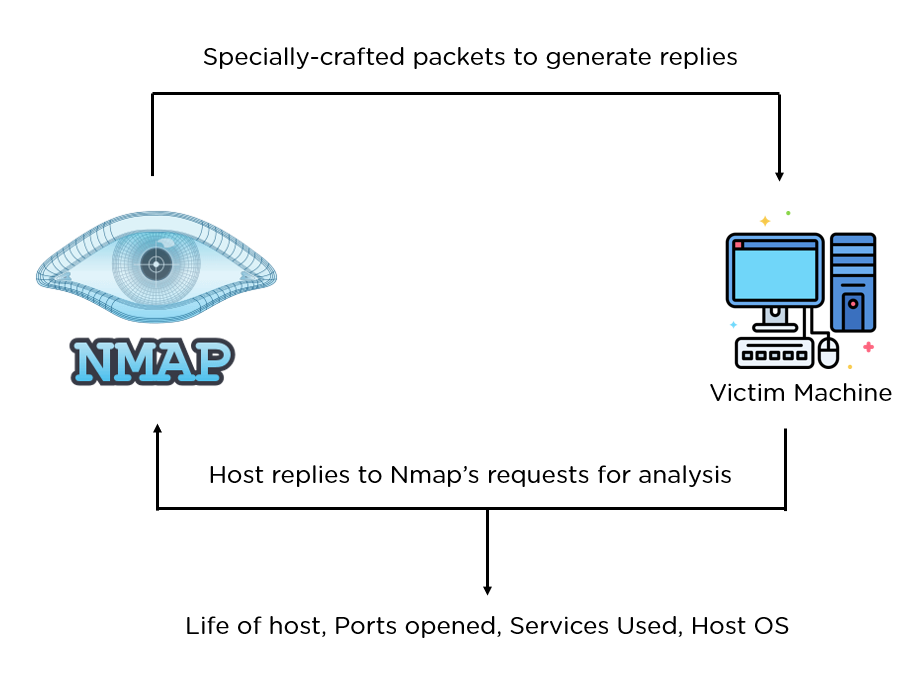
Nmap, short for Network Mapper, is a powerful open-source tool used for network exploration, security auditing, and more. It is widely used by network administrators and security professionals to discover hosts and services on a computer network, thus creating a "map" of the network. This guide will walk you through the installation, basic usage, and advanced features of Nmap.
1. Introduction to Nmap
Nmap is designed to scan large networks quickly, but it can also be used against single hosts. It uses raw IP packets in novel ways to determine:
- What hosts are available on the network
- What services (application name and version) those hosts are offering
- What operating systems (and OS versions) they are running
- What type of packet filters/firewalls are in use
2. Installation
On Linux
Most Linux distributions include Nmap in their repositories. You can install it using the package manager:
CentOS/Fedora:
sudo dnf install nmap
Ubuntu/Debian:
sudo apt-get install nmap
On Windows
- Download the Installer: Get the latest version from the Nmap download page.
- Run the Installer: Follow the prompts to install Nmap and optionally Zenmap (the graphical interface).
On macOS
- Download the Installer: Get the .mpkg file from the Nmap download page.
- Run the Installer: Follow the installation steps.
3. Basic Usage
Launching Nmap
Open a terminal or command prompt and type:
nmap
This will display the basic usage information and options.
Basic Scans
Operating System Detection: To identify the operating system of the target.
nmap -O <target>
Example:
nmap -O 192.168.1.1
Service Version Detection: To detect the version of services running on open ports.
nmap -sV <target>
Example:
nmap -sV 192.168.1.1
Port Scan: To scan for open ports on a host.
nmap -p <port> <target>
Example:
nmap -p 80,443 192.168.1.1
Ping Scan: To check if a host is up.
nmap -sn <target>
Example:
nmap -sn 192.168.1.1
4. Advanced Usage
Scanning Multiple IPs
You can scan multiple IP addresses or ranges in a single command:
nmap 192.168.1.1 192.168.1.2 192.168.1.3
Or use a range:
nmap 192.168.1.1-10
Aggressive Scanning
Aggressive scanning combines OS detection, version detection, script scanning, and traceroute:
nmap -A <target>
Example:
nmap -A 192.168.1.1
Output Options
Save the scan results to a file:
Grepable Output:
nmap -oG output.gnmap <target>
XML Output:
nmap -oX output.xml <target>
Normal Output:
nmap -oN output.txt <target>
5. Nmap Scripting Engine (NSE)
Nmap includes a powerful scripting engine that can be used to write custom scripts for various tasks.
Run a Specific Script:
nmap --script <script_name> <target>
Example:
nmap --script http-enum 192.168.1.1
List Available Scripts:
ls /usr/share/nmap/scripts/
6. Zenmap - The GUI for Nmap
Zenmap is the official graphical user interface (GUI) for Nmap. It is useful for beginners and for visualizing scan results.
- Launching Zenmap:
Open Zenmap from your applications menu or typezenmapin the terminal. - Performing a Scan:
Enter the target IP and select a scan profile (e.g., Quick Scan, Intense Scan).
7. Best Practices
- Legal Considerations: Only scan networks and hosts you own or have explicit permission to scan.
- Use in Isolated Environments: Perform scans in a controlled and isolated environment to avoid unintended disruptions.
Regular Updates: Keep Nmap updated to access the latest features and scripts.
sudo apt-get update && sudo apt-get upgrade nmap
8. Learning Resources
- Official Documentation: Nmap Documentation
- Community Forums: Engage with the community on forums and mailing lists.
- Online Tutorials: Platforms like freeCodeCamp and YouTube offer comprehensive tutorials on Nmap.
Conclusion
Nmap is an indispensable tool for network administrators and security professionals. By following this guide, you should be well on your way to mastering Nmap and leveraging its full potential for network exploration and security auditing. For more detailed tutorials, screenshots, and videos, refer to the official documentation and community resources.
Citations:
[1] https://nmap.org/book/intro.html
[2] https://www.liquidweb.com/blog/using-nmap-pro-tips-and-tricks/
[3] https://www.holmsecurity.com/blog/what-is-nmap
[4] https://www.freecodecamp.org/news/what-is-nmap-and-how-to-use-it-a-tutorial-for-the-greatest-scanning-tool-of-all-time/
[5] https://nmap.org/book/inst-windows.html
[6] https://nmap.org/book/inst-linux.html
[7] https://www.recordedfuture.com/threat-intelligence-101/tools-and-techniques/nmap-commands
[8] https://www.varonis.com/blog/nmap-commands
[9] https://hackertarget.com/nmap-tutorial/
[10] https://nmap.org/book/resources.html