Comprehensive Defensive Strategies for Linux Security

Introduction:
In the rapidly evolving cyber threat landscape, Linux systems require robust defense mechanisms to protect against unauthorized access, data breaches, and other malicious activities. The multi-layered approach to Linux security involves an array of tools and technologies, each serving a unique purpose in the broader security protocol. This article delves into the critical components of defensive Linux security, providing insights that can be invaluable in cybersecurity sales materials.
Cyber Sales Advisor GPT
https://chat.openai.com/g/g-LlTzr1MId-cyber-sales-advisor/
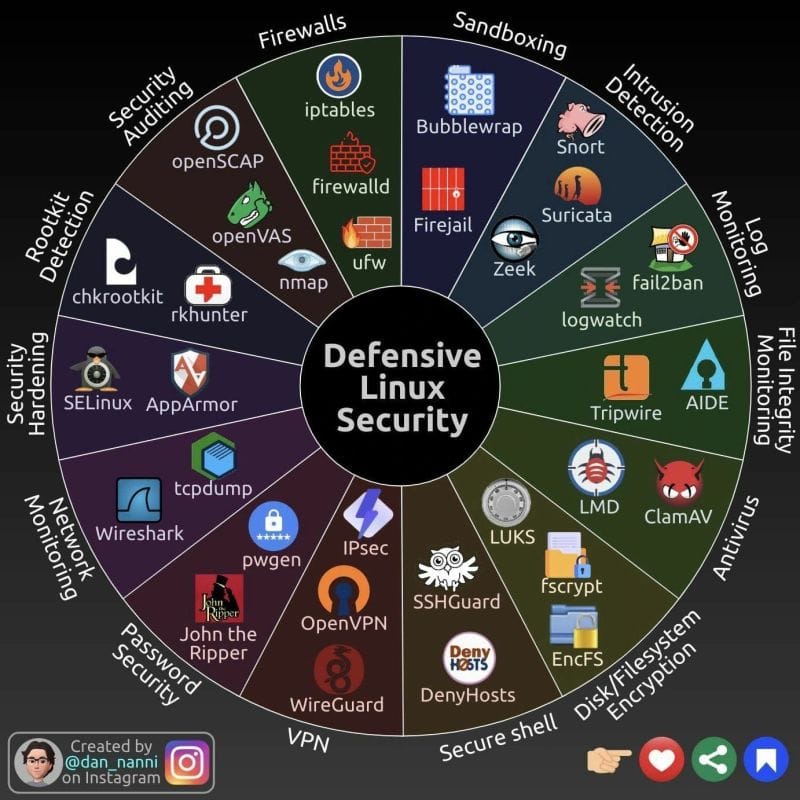
Firewalls:
- iptables: A command-line firewall utility that allows system administrators to configure rules for incoming and outgoing traffic.
- firewalld: A dynamic firewall manager with support for network/firewall zones to define the trust level of network connections or interfaces.
- ufw: An easy-to-use interface for iptables, offering a simplified method to create firewall rules.
Sandboxing:
- Bubblewrap: A sandboxing tool that creates secure isolation for running applications, minimizing the risk of system tampering.
- Firejail: Enhances the security of Linux systems by restricting the running environment of untrusted applications.
Intrusion Detection:
- Snort: An open-source network intrusion detection system (NIDS) that can detect and prevent intrusions by monitoring network traffic.
- Suricata: A robust network threat detection engine capable of real-time intrusion detection (IDS), intrusion prevention (IPS), and network security monitoring.
Logging and Monitoring:
- Zeek: A powerful network analysis framework focused on security monitoring, suitable for detecting complex behaviors.
- logwatch: A customizable log analysis system that parses through your system's logs and creates a report analyzing areas that you specify.
Rootkit Detection:
- chkrootkit: A tool to locally check for signs of a rootkit on a Unix-like system.
- rkhunter: A Unix-based tool that scans for rootkits, backdoors, and possible local exploits.
Security Auditing:
- openSCAP: An auditing tool that provides a line of defense against security weaknesses in the system configuration.
- SELinux: Security-Enhanced Linux provides a mechanism for supporting access control security policies, including mandatory access controls (MAC).
VPN and Secure Shell:
- OpenVPN: A robust and highly flexible VPN daemon that uses all of the encryption, authentication, and certification features of the OpenSSL library.
- WireGuard: A simple yet fast and modern VPN that utilizes state-of-the-art cryptography.
- SSHGuard: Protects hosts from brute-force attacks against SSH and other services using ipfw/nftables/iptables firewall systems.
Conclusion:
When it comes to Linux security, no single solution can provide complete protection. A layered security strategy leveraging these tools can greatly enhance the defense mechanisms of Linux systems. For cybersecurity sales professionals, an understanding of these tools not only helps in conveying the technical proficiency of the products but also demonstrates how they can integrate into potential clients' existing security infrastructures, reinforcing the value proposition.
In a sales context, this material can be adapted into brochures, datasheets, and presentations to help clients understand the importance of each tool and how they collectively form a comprehensive security solution for their Linux environments.







