DevSecOps vs SecDevOps: Stop Using Them Interchangeably (They're Not the Same Thing!)
If you've ever found yourself in a meeting where people are talking about "DevSecOps" but you suspect they mean completely different things, you're not alone. The cybersecurity industry has a habit of using DevSecOps and SecDevOps interchangeably, but here's the thing: they're actually two distinct approaches solving different problems.

Let's clear up this confusion once and for all, because mixing these up can lead to some seriously frustrating conversations where everyone thinks they're on the same page, but you're actually discussing completely different methodologies.
The Simple Distinction That Changes Everything
Before we dive deep, here's the core difference that will save you from countless miscommunications:
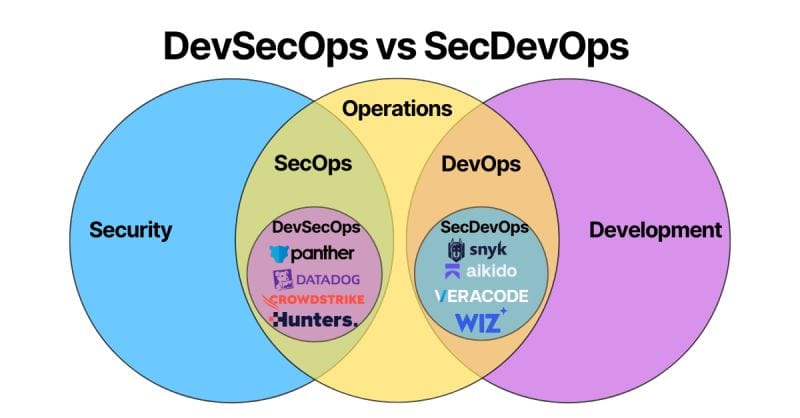
- Security for DevOps = SecDevOps (Security integrated into Development Operations)
- Development for SecOps = DevSecOps (Development practices applied to Security Operations)
Think of it this way: the first word tells you which domain is being enhanced by the second. SecDevOps enhances development with security, while DevSecOps enhances security operations with development practices.
DevSecOps: Bringing Development Practices to Security Operations
What It Actually Means
DevSecOps is about taking the successful methodologies from software development and applying them to security operations. It's Development for Security Operations – essentially asking "How can we make security teams work more like development teams?"
This approach recognizes that security operations can benefit enormously from the practices that have revolutionized software development: version control, automation, infrastructure as code, and continuous integration/continuous deployment (CI/CD).

What DevSecOps Looks Like in Practice
When you implement DevSecOps, you're empowering your security analysts to work like developers:
Code-Driven Security Operations:
- Writing detection rules using programming languages like Python
- Creating detection logic with standardized formats like Sigma rules
- Building configurations in YAML for easier management
- Leveraging frameworks like PySigma for rule conversion and management
Automation and Integration:
- Developing custom automation scripts for repetitive security tasks
- Building integrations between security tools using APIs
- Creating automated response playbooks that can be version-controlled
- Developing custom connectors for data ingestion and tool orchestration
Infrastructure as Code for Security:
- Codifying SIEM deployments so they can be reproduced and scaled
- Storing security infrastructure configurations in version control
- Managing security tool configurations through code repositories
- Implementing security infrastructure changes through CI/CD pipelines
Developer-Style Workflows:
- Using Git repositories to manage security detection rules and playbooks
- Implementing code review processes for security automation
- Version controlling security configurations and detection logic
- Collaborating on security tools through familiar development workflows
DevSecOps Tools and Platforms
The security industry has responded to this need with platforms that embrace development practices:
- CrowdStrike Falcon: Offers extensive API access and automation capabilities
- Hunters: Provides code-based detection engineering and automation
- Panther: Built specifically for security teams who want to work with code
- Datadog Security Monitoring: Integrates security monitoring with development workflows
- Microsoft Sentinel: Offers robust automation and custom development capabilities
These platforms recognize that modern security teams need to be able to treat their detection logic, automation scripts, and infrastructure configurations like any other codebase.
SecDevOps: Shifting Security Left in Development
What It Actually Means
SecDevOps is the more commonly discussed approach – it's Security for Development Operations. This methodology focuses on integrating security practices earlier in the software development lifecycle, often called "shifting left."
The core principle is simple: instead of treating security as a gate at the end of development, embed security considerations throughout the entire development process.
What SecDevOps Looks Like in Practice
SecDevOps implementation focuses on making security an integral part of development workflows:
Security Testing Integration:
- Static Application Security Testing (SAST) integrated into the development environment
- Dynamic Application Security Testing (DAST) running in staging environments
- Interactive Application Security Testing (IAST) providing real-time feedback during development
- Container and infrastructure security scanning as part of the build process
Automated Security in CI/CD:
- Security scans triggered automatically on code commits
- Automated vulnerability assessments in CI/CD pipelines
- Security gate checks that prevent insecure code from reaching production
- Automated compliance checking against security policies
Dependency and Composition Security:
- Software Composition Analysis (SCA) to identify vulnerable dependencies
- License compliance checking for open source components
- Automated updates for security patches in dependencies
- Supply chain security monitoring and verification
Infrastructure Security:
- Infrastructure as Code (IaC) security scanning
- Cloud configuration security analysis
- Policy enforcement for infrastructure deployments
- Automated compliance checking for cloud resources
API and Application Security:
- Automated API security testing and scanning
- Runtime application protection and monitoring
- Security-focused code analysis and review
- Credential scanning to prevent hardcoded secrets
SecDevOps Tools and Platforms
The SecDevOps ecosystem includes tools designed to integrate seamlessly into development workflows:
- Snyk: Comprehensive vulnerability scanning for code, dependencies, and infrastructure
- Wiz: Cloud security platform focusing on development and deployment security
- Veracode: Application security testing integrated into development processes
- Aikido Security: Developer-first security platform for comprehensive application protection
These tools are designed with developers in mind, providing security insights in formats and workflows that development teams can easily adopt.
Why the Distinction Matters
Different Teams, Different Problems
The confusion between these terms isn't just semantic – it reflects different organizational needs:
- DevSecOps is primarily valuable for security teams who want to adopt modern development practices
- SecDevOps is primarily valuable for development teams who need to integrate security into their workflows
Different Skill Requirements
Each approach requires different skill development:
DevSecOps Skills:
- Security analysts learning programming languages
- Understanding of CI/CD concepts for security operations
- Familiarity with infrastructure as code principles
- API integration and automation development skills
SecDevOps Skills:
- Developers learning security testing methodologies
- Understanding security vulnerabilities and remediation
- Integration of security tools into existing development workflows
- Security-aware coding practices and secure design principles
Different Success Metrics
The success of each approach is measured differently:
DevSecOps Success Metrics:
- Reduction in mean time to detection and response
- Increased automation coverage for security operations
- Improved consistency in security tool configurations
- Enhanced collaboration between security and operations teams
SecDevOps Success Metrics:
- Reduction in vulnerabilities reaching production
- Faster vulnerability remediation times
- Increased developer security awareness and adoption
- Improved compliance with security policies in development
Implementation Strategies
Starting with DevSecOps
If you're looking to implement DevSecOps in your security operations:
- Assess Your Current State: Evaluate how much of your security operations relies on manual processes
- Identify Automation Opportunities: Look for repetitive tasks that could be scripted
- Start Small: Begin with simple automation projects like automated alert creation
- Build Skills: Invest in training your security team on programming and automation
- Choose the Right Platform: Select security tools that support API access and automation
Starting with SecDevOps
If you're looking to implement SecDevOps in your development process:
- Security Tool Integration: Start by integrating security scanning into your existing CI/CD pipeline
- Developer Education: Train your development team on security best practices
- Policy as Code: Implement security policies that can be automatically enforced
- Incremental Adoption: Gradually increase the security requirements and automation
- Feedback Loops: Ensure security findings are presented in developer-friendly formats
The Future of Both Approaches
Convergence Without Confusion
While DevSecOps and SecDevOps remain distinct approaches, successful organizations often implement both:
- Security teams adopt development practices (DevSecOps) to become more efficient and scalable
- Development teams integrate security practices (SecDevOps) to build more secure software
The key is understanding which approach you're discussing and implementing, rather than assuming they're the same thing.
Organizational Maturity
As organizations mature in their security practices, they often find value in both approaches:
- Early Stage: Focus on SecDevOps to prevent security issues from reaching production
- Intermediate Stage: Implement DevSecOps to scale security operations effectively
- Advanced Stage: Seamlessly integrate both approaches for comprehensive security coverage
Conclusion
The next time someone mentions "DevSecOps" in a meeting, take a moment to clarify whether they mean security for development operations (SecDevOps) or development for security operations (DevSecOps). This small clarification can save hours of miscommunication and ensure everyone is working toward the same goals.
Remember: these aren't just different names for the same concept – they're distinct methodologies addressing different challenges in modern cybersecurity. SecDevOps helps developers build more secure software, while DevSecOps helps security teams operate more like modern development teams.
Both are valuable, both are necessary, and both deserve to be understood and implemented correctly. Stop using them interchangeably, and start implementing them strategically based on your organization's specific needs.
The cybersecurity industry will thank you for the clarity, and your teams will thank you for the improved collaboration and effectiveness that comes from understanding exactly what you're trying to achieve.







