The Full-Stack Atmosphere: A Secure Coding Journey

In today's interconnected digital landscape, full-stack development plays a crucial role in building robust, efficient, and secure applications. The image you've provided gives us a glimpse into the vast ecosystem of tools and technologies involved in full-stack development. However, as we dive deeper into the "Full-Stack Atmosphere," it's essential to highlight secure coding practices, Software Development Life Cycle (SDLC) considerations, and the OWASP Top 10 guidelines to ensure the creation of secure and resilient applications.
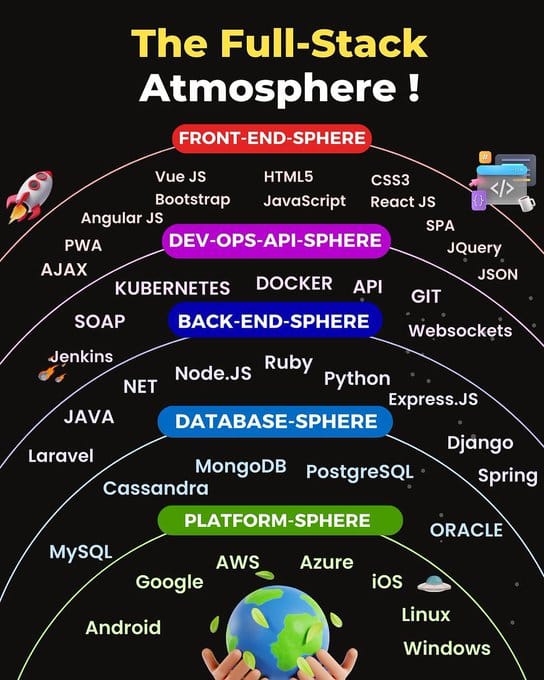
Understanding the Full-Stack Layers
The "Full-Stack Atmosphere" is divided into several key layers, each representing different aspects of application development:
- Front-End Sphere: This includes technologies such as HTML5, CSS3, JavaScript, AngularJS, ReactJS, and Bootstrap. These tools are essential for building the user interface (UI) and ensuring a seamless user experience (UX).
- DevOps-API Sphere: This layer encompasses DevOps tools and API management frameworks like Kubernetes, Docker, SOAP, REST, GIT, and Jenkins. These tools streamline development, deployment, and operations.
- Back-End Sphere: Here, we find server-side languages and frameworks like Node.js, Python, Ruby, Java, .NET, and Express.js. These technologies handle business logic, database interactions, and server-side processing.
- Database Sphere: This includes database management systems (DBMS) like MongoDB, PostgreSQL, MySQL, Oracle, and Cassandra, which are crucial for data storage, retrieval, and management.
- Platform Sphere: This final layer comprises the operating systems, cloud platforms, and environments where applications are hosted, such as AWS, Azure, Google Cloud, Linux, Windows, Android, and iOS.



Integrating Secure Coding Practices
As developers traverse these layers, secure coding practices must be ingrained at every step. Here's how to incorporate security into each sphere:
1. Front-End Sphere: Securing the UI
- Input Validation: Implement rigorous input validation to prevent Cross-Site Scripting (XSS) and other client-side attacks. Ensure that user inputs are sanitized and validated before processing.
- Content Security Policy (CSP): Deploy CSP headers to mitigate the risk of XSS by controlling the sources from which content can be loaded.
- Session Management: Securely manage user sessions using secure cookies, implementing HttpOnly, Secure, and SameSite flags to prevent session hijacking.
2. DevOps-API Sphere: Security in Deployment
- Secure APIs: Apply OAuth2, OpenID Connect, and API gateways to manage and authenticate API access securely. Encrypt API traffic using TLS.
- CI/CD Pipeline Security: Integrate security checks into your CI/CD pipeline. Tools like Snyk and OWASP Dependency-Check can identify vulnerabilities in dependencies during the build process.
- Infrastructure as Code (IaC): Secure your IaC (e.g., Terraform, Ansible) by enforcing strict access controls and validating configurations against security benchmarks.
3. Back-End Sphere: Server-Side Security
- Authentication and Authorization: Implement strong authentication mechanisms (e.g., Multi-Factor Authentication) and role-based access controls to safeguard back-end services.
- Error Handling: Avoid revealing sensitive information in error messages. Implement custom error pages that provide minimal information to prevent information leakage.
- Security Headers: Utilize security headers like X-Frame-Options, X-Content-Type-Options, and Strict-Transport-Security to protect against common attacks such as clickjacking and MIME sniffing.
4. Database Sphere: Securing Data
- Encryption: Encrypt sensitive data at rest using Transparent Data Encryption (TDE) and encrypt data in transit using TLS to prevent unauthorized access.
- Least Privilege: Apply the principle of least privilege when configuring database access, ensuring that users and applications only have the minimum permissions necessary.
- Regular Auditing: Regularly audit database activities to detect and respond to any unauthorized access or suspicious activities.
5. Platform Sphere: Secure Hosting
- Environment Hardening: Harden your OS and cloud environments by disabling unnecessary services, applying patches regularly, and following the Center for Internet Security (CIS) benchmarks.
- Logging and Monitoring: Implement centralized logging and real-time monitoring to detect and respond to security incidents promptly. Tools like ELK stack and Prometheus can be invaluable.
- Backup and Recovery: Regularly back up critical data and configurations, and ensure that recovery procedures are well-documented and tested.
Incorporating Secure SDLC
A secure Software Development Life Cycle (SDLC) ensures that security is embedded throughout the development process. Here's how to integrate security into each SDLC phase:
- Planning: Identify security requirements and potential threats early in the planning phase. Define security goals and create a risk management plan.
- Design: Incorporate security principles such as least privilege, defense in depth, and secure design patterns into the architecture.
- Implementation: Write secure code by adhering to secure coding guidelines. Conduct peer reviews and use static code analysis tools to identify vulnerabilities.
- Testing: Perform security testing, including penetration testing, fuzz testing, and vulnerability scanning. Tools like OWASP ZAP and Burp Suite can assist in identifying security flaws.
- Deployment: Ensure secure configurations are applied during deployment, and conduct post-deployment security assessments to validate security measures.
- Maintenance: Regularly update and patch the application, monitor for new vulnerabilities, and perform periodic security reviews.
Addressing the OWASP Top 10
The OWASP Top 10 is a critical set of guidelines that every developer should be familiar with. Here’s how to address the most common vulnerabilities across the full-stack:
- Injection: Prevent SQL, NoSQL, and OS command injection by using parameterized queries and ORM frameworks.
- Broken Authentication: Implement strong password policies, Multi-Factor Authentication (MFA), and secure session management practices.
- Sensitive Data Exposure: Encrypt sensitive data both in transit and at rest, and avoid exposing it in logs or error messages.
- XML External Entities (XXE): Disable external entity processing in XML parsers and use less complex data formats like JSON.
- Broken Access Control: Enforce robust access controls and validate them with thorough testing to prevent unauthorized access.
- Security Misconfiguration: Regularly update and patch software, and use automated tools to detect and rectify misconfigurations.
- Cross-Site Scripting (XSS): Implement input validation, escape output, and use security frameworks that automatically sanitize user inputs.
- Insecure Deserialization: Avoid deserializing untrusted data and implement integrity checks to validate serialized data.
- Using Components with Known Vulnerabilities: Regularly update libraries and frameworks, and use tools to scan for vulnerable dependencies.
- Insufficient Logging and Monitoring: Implement comprehensive logging and monitoring to detect and respond to security incidents promptly.
Conclusion
Navigating the "Full-Stack Atmosphere" requires a thorough understanding of the technologies involved and the security implications at each layer. By integrating secure coding practices, adhering to a secure SDLC, and addressing the OWASP Top 10, developers can build resilient applications that stand up to the challenges of today’s threat landscape. Security should not be an afterthought but a fundamental aspect of every decision made throughout the development process.
This article has covered the essential aspects of securing the full-stack, but continuous learning and adaptation to new threats are crucial. Stay updated with the latest security practices, and ensure that security is embedded in the DNA of your development efforts.






