Bluetooth Low Energy (BLE) in Modern Automotive Systems

Bluetooth Low Energy (BLE) has become a critical component in modern automotive systems, enabling energy-efficient connectivity while introducing new attack surfaces. Below we examine BLE's automotive applications, associated vulnerabilities, and fuzzing techniques for security analysis.

BLE in Modern Automotive Systems
Modern vehicles implement BLE in these key areas:
1. Smart Vehicle Access (Virtual Keys)
Smartphone-based digital keys using BLE enable:
- Phone-as-key functionality for lock/unlock/engine start[2][6]
- Secure car-sharing platforms with temporary access grants[2]
- Proximity-based authentication (3-10m range)[18]
2. Battery Management Systems
EVs leverage BLE for:
- Real-time battery pack voltage/temperature monitoring[14][20]
- Wireless communication with charging stations[14]
- Reduced wiring complexity in battery arrays[2]
3. In-Vehicle Personalization
BLE enables driver-specific profiles for:
- Seat/mirror/steering wheel adjustments[2][6]
- Infotainment preferences (radio presets, EQ settings)[2]
- Climate control configurations[18]

4. Diagnostic & Maintenance Systems
BLE facilitates:
- Wireless OBD-II dongles for telematics[6]
- Tire pressure monitoring (TPMS)[6][14]
- Predictive maintenance alerts[2]
5. Cable Replacement
BLE eliminates physical wiring for:
- Power seat/window/mirror controls[2]
- Trunk release mechanisms[6]
- Sunroof actuators[2]

BLE Security Vulnerabilities
Recent research reveals three primary attack vectors:
| Vulnerability Type | Impact | Example CVEs |
|---|---|---|
| Device Tracking | Location privacy breach | CVE-2020-12856[4] |
| Eavesdropping | Data interception | CVE-2019-19196[5] |
| MITM Attacks | Session hijacking | CVE-2020-15802[7] |
Notable automotive-specific risks:
- SweynTooth vulnerabilities affecting NXP/TI chipsets (CVE-2019-17519, CVE-2019-19192)[5][7]
- Key Negotiation flaws in pairing processes[4][9]
- GATT layer spoofing through malformed attributes[8]

Fuzzing Methodology for BLE Systems
The WHAD framework provides a structured approach for BLE fuzzing:
1. Protocol Analysis
- Map GATT service hierarchy[8][22]
- Identify ATT operations (read/write/notify)[34]
- Document SMP pairing procedures[5]
2. Fuzzer Configuration
from whad import BleScanner
from whad.protocol.ble import BleConnection
scanner = BleScanner()
scanner.start()
device = scanner.discover('VEHICLE_BLE_MAC')
conn = BleConnection(device)
conn.connect()
3. Attack Vectors
- Stateful Fuzzing: Maintain connection context across tests[25]
- PDU Mutation: Manipulate header fields and payloads[8]
- Timing Attacks: Exploit connection interval widening[5]
4. Anomaly Detection
Monitor for:
- Unexpected disconnects
- Memory leakage patterns
- Invalid response codes (0x01-0xFF)[34]

Case Study: SweynTooth Findings
Texas Instruments CC2640 implementations exhibited:
- Invalid LL Control Parsing leading to deadlocks[5]
- Key Size Overflow in SMP layer (CVE-2019-19196)[5]
- LLID Field Manipulation causing buffer overflows[23]
Mitigation Strategies
- Secure Pairing: Enforce LE Secure Connections (LESC)[9]
- Input Validation: Sanitize ATT MTU sizes[8]
- Firmware Updates: Implement secure OTA mechanisms[6]
- Protocol Hardening: Use BLE 5.1+ with angle-of-arrival security[37]
Automotive manufacturers like NXP and TI now offer AEC-Q100 certified BLE SoCs with hardware-based cryptographic accelerators and secure boot capabilities[6][20]. Regular penetration testing using frameworks like WHAD and BTFuzzer[21] has become essential in vehicle development cycles.
The combination of BLE's low-power advantages and automotive connectivity demands creates both opportunities and security challenges. As demonstrated by recent research, systematic fuzzing approaches combined with protocol-aware analysis remain the most effective way to identify vulnerabilities in complex BLE implementations[8][23].

https://hardwear.io/netherlands-2024/presentation/ble-gatt-fuzzing-bboyer.pdf
https://www.ti.com/lit/wp/sway008/sway008.pdf
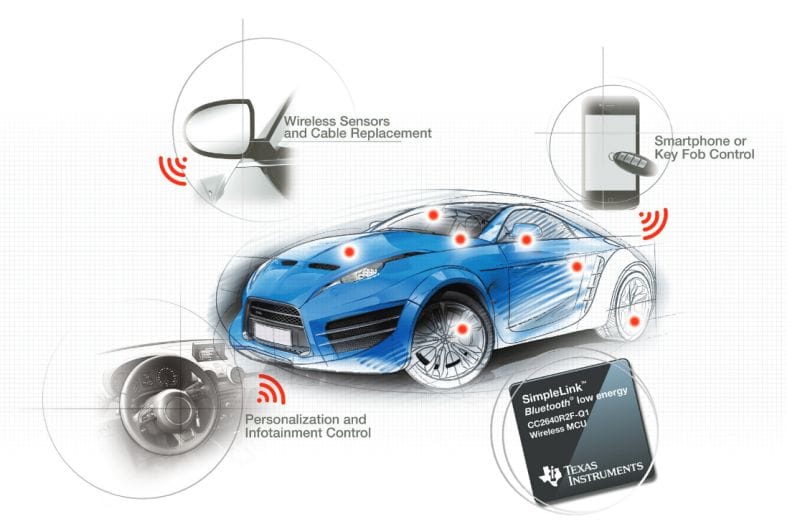
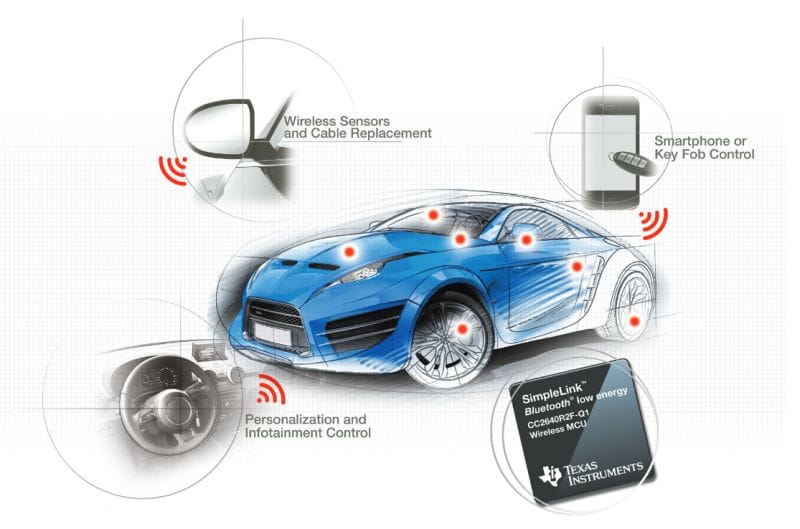
Key BLE Integration Points
Wireless Sensors and Cable ReplacementThe upper left bubble shows how BLE eliminates traditional wiring by enabling wireless communication for various vehicle sensors, reducing weight and complexity in the vehicle's electrical system.Smartphone/Key Fob IntegrationThe upper right bubble demonstrates the smart access capabilities, where BLE enables:
- Digital key functionality through smartphones
- Traditional key fob communication
- Secure vehicle access control
Interior SystemsThe lower left bubble highlights the personalization and infotainment control features:
- Driver preference settings
- Entertainment system controls
- Climate control adjustments
Hardware ImplementationThe lower right corner shows a Texas Instruments SimpleLink™ BLE chip, which is specifically designed for automotive applications with:
- Low energy consumption
- Wireless MCU capabilities
- Automotive-grade specifications
Technical Implementation
The red dots scattered across the vehicle's body indicate various BLE connection points, demonstrating the comprehensive coverage of wireless connectivity throughout the vehicle's systems. This distributed network of BLE sensors and controllers creates a sophisticated ecosystem for vehicle monitoring, control, and user interaction.The technical illustration effectively shows how BLE technology serves as a cornerstone for modern automotive connectivity, enabling both convenience features and essential vehicle functions while maintaining energy efficiency.
Citations:
[1] https://www.techtarget.com/iotagenda/definition/Bluetooth-Low-Energy-Bluetooth-LE
[2] https://www.ti.com/lit/wp/sway008/sway008.pdf?ts=1703416462553
[3] https://www.minewtag.com/5-features-of-bluetooth-low-energy.html
[4] https://www.allaboutcircuits.com/technical-articles/vulnerabilities-and-attacks-on-bluetooth-le-devicesreviewing-recent-info/
[5] https://asset-group.github.io/papers/SweynTooth.pdf
[6] https://www.edn.com/secure-bluetooth-le-adoption-on-rise-in-automotive-applications/
[7] https://www.thyrasec.com/blog/top-6-bluetooth-vulnerabilities/
[8] https://blog.quarkslab.com/bluetooth-low-energy-gatt-fuzzing.html
[9] https://www.einfochips.com/blog/bluetooth-low-energy-ble-security-and-privacy-for-iot/
[10] https://www.bluetooth.com/bluetooth-resources/bluetooth-low-energy-and-the-automotive-transformation/
[11] https://response.nordicsemi.com/the-complete-guide-to-bluetooth-low-energy
[12] https://www.bluetooth.com/bluetooth-resources/exploring-connectivity-trends-car/
[13] https://litum.com/what-is-ble-how-does-ble-work/
[14] https://semiengineering.com/the-proliferation-of-bluetooth-in-v2x-automotive-applications/
[15] https://www.silabs.com/documents/public/user-guides/ug103-14-fundamentals-ble.pdf
[16] https://www.youtube.com/watch?v=aXRSmuHdaZ8
[17] https://developer.android.com/develop/connectivity/bluetooth/ble/ble-overview
[18] https://www.renesas.com/en/blogs/ask-experts-how-bluetooth-low-energy-enabling-keyless-future-drivers
[19] https://learn.adafruit.com/introduction-to-bluetooth-low-energy/introduction
[20] https://www.nxp.com/company/about-nxp/smarter-world-blog/BL-AUTOMOTIVE-BLE
[21] https://yonghwi-kwon.github.io/data/btfuzzer_icisc23.pdf
[22] https://blog.quarkslab.com/tag/ble.html
[23] https://www.usenix.org/system/files/sec22-garbelini.pdf
[24] https://bluegoatcyber.com/blog/top-ble-cybersecurity-vulnerabilities/
[25] https://git.ist.tugraz.at/apferscher/ble-fuzzing
[26] https://github.com/Charmve/BLE-Security-Attack-Defence
[27] https://www.bluetooth.com/learn-about-bluetooth/key-attributes/bluetooth-security/reporting-security/
[28] https://stackoverflow.com/questions/54584087/bluetooth-low-energy-fuzzing
[29] https://cybervelia.com/ble-pentest
[30] https://ieeexplore.ieee.org/document/7804832/
[31] https://gigvvy.com/journals/cccisa/articles/security-fuzz-testing
[32] https://hardwear.io/netherlands-2024/speakers/baptiste-boyer.php
[33] https://cve.mitre.org/cgi-bin/cvekey.cgi
[34] https://hardwear.io/netherlands-2024/presentation/ble-gatt-fuzzing-bboyer.pdf
[35] https://www.link-labs.com/blog/bluetooth-vs-bluetooth-low-energy
[36] https://www.linkedin.com/pulse/bluetooth-low-energy-ble-power-efficient-connectivity-solution-kmvfc
[37] https://www.bluetooth.com/learn-about-bluetooth/tech-overview/
[38] https://novelbits.io/bluetooth-low-energy-ble-complete-guide/
[39] https://www.usenix.org/system/files/sec22_slides-garbelini.pdf