Securing Containerized Applications

Container security is a multi-faceted discipline focusing on securing containerized applications and the environments they run in. Below, I'll expand on each category presented in the diagram and provide additional context.
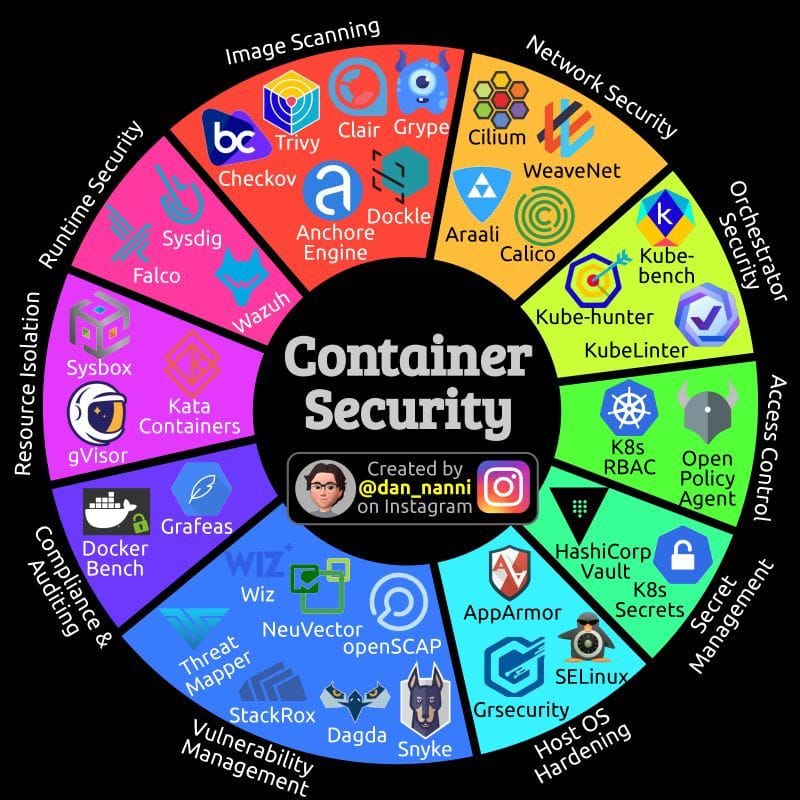
1. Image Scanning
- Purpose: Tools in this category are designed to scan container images for vulnerabilities, malware, and configuration issues before they are deployed.
- Tools:
- Trivy: A comprehensive and easy-to-use tool for scanning container images for known vulnerabilities.
- Clair: A tool for static analysis of vulnerabilities in application containers (primarily Docker).
- Grype: A vulnerability scanner for container images and filesystems with support for various formats.
- Checkov: Focuses on scanning for security issues in cloud infrastructure (not strictly limited to containers but applicable).
- Anchore Engine: A service that allows you to inspect, analyze, and certify container images.
- Dockle: A container linter focusing on best practices for Docker container image production.

2. Network Security
- Purpose: Tools that ensure secure networking practices and policies for containerized environments.
- Tools:
- Cilium: Provides secure network connectivity between application services deployed using Linux container management platforms like Docker and Kubernetes.
- WeaveNet: A simple, resilient network for Docker containers, useful for securing traffic between containers.
- Araali: Focuses on micro-segmentation to secure workloads across clouds and containers.
- Calico: A widely used networking and network security solution for containers, VMs, and workloads.
3. Orchestrator Security
- Purpose: These tools focus on securing the orchestration layer, typically Kubernetes, which manages the deployment and scaling of containers.
- Tools:
- Kube-bench: Checks whether Kubernetes is deployed securely by running checks aligned with the CIS Kubernetes Benchmark.
- Kube-hunter: A penetration testing tool that simulates attacks on a Kubernetes cluster.
- KubeLinter: A static analysis tool to check Kubernetes YAML files for best practices and security issues.

4. Access Control
- Purpose: Access control tools help manage permissions and enforce security policies within a containerized environment.
- Tools:
- K8s RBAC: Role-Based Access Control (RBAC) is a method of regulating access to computer or network resources based on the roles of individual users within your Kubernetes cluster.
- Open Policy Agent (OPA): A general-purpose policy engine that enables you to enforce policies across your stack.

5. Secret Management
- Purpose: Tools for managing and securing secrets (like passwords, tokens, certificates) that are used by applications within containers.
- Tools:
- HashiCorp Vault: A tool for securely storing and accessing secrets and sensitive data.
- K8s Secrets: Kubernetes-native method to store and manage sensitive information within a Kubernetes cluster.
6. Host OS Hardening
- Purpose: Tools and techniques for hardening the underlying operating system to reduce the attack surface for containers.
- Tools:
- AppArmor: A Linux security module that allows the system administrator to restrict the capabilities of programs.
- SELinux: Security-Enhanced Linux is a set of kernel modifications and user-space tools that provide a mechanism for supporting access control security policies.
- Grsecurity: A set of patches for the Linux kernel with an emphasis on enhancing security.
7. Vulnerability Management
- Purpose: Tools that focus on managing and mitigating vulnerabilities in container environments.
- Tools:
- Wiz: A cloud security platform that helps in identifying and remediating vulnerabilities.
- NeuVector: A Kubernetes-native container security platform providing vulnerability scanning and compliance enforcement.
- openSCAP: A tool that provides compliance checking for various policies like CIS, NIST, etc.
- Threat Mapper: Focuses on identifying and mitigating threats within the Kubernetes environment.
- StackRox: A Kubernetes-native security platform that detects and mitigates risks in containerized applications.
- Dagda: An open-source tool for performing static analysis of known vulnerabilities in Docker images.
- Snyk: Focuses on vulnerability scanning and fixing, specifically for open-source dependencies.
8. Compliance & Auditing
- Purpose: Tools that ensure containerized applications and environments adhere to regulatory standards and best practices.
- Tools:
- Grafeas: An open-source artifact metadata API to audit and govern software supply chain.
- Docker Bench: A script that checks for dozens of common best practices around deploying Docker containers.
9. Resource Isolation
- Purpose: Tools that ensure proper isolation of resources (CPU, memory, etc.) between different containers to prevent unauthorized access or attacks.
- Tools:
- Sysbox: A runtime that improves container isolation by providing stronger boundaries between containers.
- Kata Containers: Combines the speed of containers with the security of VMs to offer better isolation.
- gVisor: A user-space kernel that implements a substantial portion of the Linux system, providing a secure isolation boundary between the application and the host.
10. Runtime Security
- Purpose: Tools that monitor and enforce security policies during the runtime of containerized applications.
- Tools:
- Sysdig: Provides runtime security, monitoring, and forensics capabilities for containerized environments.
- Falco: An open-source runtime security tool that detects anomalies in containerized environments.
- Wazuh: A security monitoring platform that includes host-based intrusion detection, log data analysis, and vulnerability detection.
Extended Container Security Sections
Cloud-Native Security
Cloud-native security integrates container security practices with the broader security landscape of cloud environments, especially in multi-cloud scenarios. Key aspects include:
- Cloud Security Posture Management (CSPM): Tools like Prisma Cloud or Fugue that continuously monitor cloud infrastructure for misconfigurations and compliance violations.
- Cloud Workload Protection Platforms (CWPP): Solutions such as Aqua Security or Trend Micro Deep Security that provide runtime protection for cloud workloads, including containers.
- Identity and Access Management (IAM): Leveraging cloud-native IAM solutions like AWS IAM, Azure AD, or Google Cloud IAM to manage access to container resources.
- Multi-Cloud Security Orchestration: Tools like Terraform or Pulumi that allow for consistent security policy application across multiple cloud environments.
In multi-cloud environments, the focus is on creating a unified security posture that spans different cloud providers, ensuring consistent policy enforcement and visibility across all container deployments.
Shift-Left Security
Shift-left security in container environments involves integrating security practices earlier in the development lifecycle. This approach includes:
- Developer Education: Training developers on secure coding practices specific to containerized applications.
- Integrated Development Environment (IDE) Plugins: Tools like Snyk's IDE plugins or Sonar Lint that provide real-time security feedback during coding.
- Pre-Commit Hooks: Implementing git hooks that run security checks before code is committed to the repository.
- Infrastructure as Code (IaC) Scanning: Using tools like Checkov or Terrascan to scan IaC templates for security issues before deployment.
- Automated Security Testing: Integrating security testing tools into CI/CD pipelines to catch vulnerabilities early in the development process.
By shifting security left, organizations can catch and address security issues earlier, reducing the cost and risk associated with fixing vulnerabilities in production environments.
Container Escapes
Container escapes occur when an attacker breaks out of the container isolation and gains access to the host system. Techniques and tools to prevent and detect container escapes include:
- Runtime Defense: Tools like Falco or Aqua Runtime Protection that monitor for suspicious activities indicative of escape attempts.
- Secure Container Runtimes: Using runtimes like gVisor or Kata Containers that provide additional isolation between containers and the host.
- Kernel Hardening: Implementing Linux Security Modules (LSMs) like AppArmor or SELinux to restrict container capabilities.
- Privileged Container Prevention: Tools and policies that prevent the creation of privileged containers or containers with dangerous capabilities.
- Escape Detection: Solutions like Sysdig Secure or Lacework that use behavioral analysis to detect potential container escapes.
Serverless Security
While serverless architectures abstract away much of the infrastructure, they often use containers under the hood. Serverless security practices include:
- Function-Level Security: Tools like PureSec (now part of Palo Alto Networks) or Protego that provide security specifically for serverless functions.
- Event Injection Prevention: Implementing input validation and sanitization to prevent malicious event data from compromising serverless functions.
- Least Privilege Execution: Ensuring serverless functions run with minimal necessary permissions using IAM roles and policies.
- Cold Start Protection: Securing the container initialization process during cold starts to prevent attackers from exploiting this window of vulnerability.
- Serverless-Specific Compliance: Adhering to guidelines like the OWASP Serverless Top 10 to address unique serverless security challenges.
AI/ML in Container Security
Artificial Intelligence and Machine Learning are increasingly being used to enhance container security:
- Anomaly Detection: AI-powered tools like Darktrace or IBM Security QRadar that can detect unusual patterns in container behavior that may indicate a security threat.
- Automated Threat Response: Machine learning models that can automatically respond to detected threats, such as isolating affected containers or applying security patches.
- Predictive Analysis: AI systems that analyze historical data to predict potential future vulnerabilities or attack vectors in containerized environments.
- Intelligent Policy Recommendation: ML-driven tools that can suggest optimal security policies based on the specific container environment and workload characteristics.
- Behavioral Analysis: Advanced AI systems that build baseline behavior profiles for containers and flag deviations that could indicate security issues.
Supply Chain Security
Securing the entire container supply chain involves:
- Software Composition Analysis (SCA): Tools like WhiteSource or Black Duck that analyze and secure open-source components used in container images.
- Signed Images: Implementing image signing and verification to ensure the integrity of container images throughout the supply chain.
- Secure Registries: Using secure container registries with features like vulnerability scanning, access controls, and image signing.
- Bill of Materials (BOM) Management: Maintaining a software bill of materials for all components in container images to track vulnerabilities and dependencies.
- Third-Party Vendor Assessment: Implementing processes to assess the security practices of third-party container image providers.
- Continuous Monitoring: Implementing tools for continuous monitoring of container images and their components for newly discovered vulnerabilities.
Regulatory Compliance
Container security practices play a crucial role in meeting regulatory requirements:
- GDPR Compliance: Implementing data protection measures like encryption at rest and in transit for containers handling EU citizen data.
- HIPAA Compliance: Ensuring proper access controls, audit logging, and encryption for containers processing healthcare data.
- PCI DSS: Implementing network segmentation, access controls, and monitoring for containers handling payment card data.
- SOC 2: Establishing and maintaining security controls for containers to meet Trust Services Criteria.
- Compliance Automation: Using tools like Twistlock (now part of Prisma Cloud) or NeuVector that provide compliance reporting and enforcement for container environments.
- Audit Trail: Implementing comprehensive logging and monitoring solutions to provide audit trails for regulatory inspections.
By addressing these aspects, organizations can create a more comprehensive and robust container security strategy that aligns with modern cloud-native architectures and regulatory requirements.
Key Considerations:
- Integration: Many of these tools can be integrated into CI/CD pipelines to ensure security is maintained throughout the development lifecycle.
- Automated Remediation: Some of these tools offer automated remediation or enforcement of security policies, reducing the manual workload on security teams.
- Compliance: Many industries require adherence to specific compliance standards, and these tools can help ensure your containerized environments meet those standards.
Container security is an evolving field, and it's essential to stay updated with the latest tools and practices. Each of these categories and tools plays a crucial role in maintaining the security, compliance, and integrity of your containerized applications and environments.







