OSINT Tutorial: A Comprehensive Guide to Open Source Intelligence

Introduction
Open Source Intelligence (OSINT) is the practice of gathering, analyzing, and using publicly available information to support decision-making, investigations, or cybersecurity operations. OSINT can be sourced from a variety of public channels such as websites, social media, online databases, forums, and more. It plays a critical role in cybersecurity, intelligence gathering, competitive analysis, and even threat detection.
This tutorial will guide you through the essential tools, techniques, and processes involved in performing OSINT investigations effectively. Whether you are a cybersecurity professional, law enforcement officer, or just an individual seeking to learn, this guide will provide you with actionable insights.

Step 1: Defining Your OSINT Objective
Before diving into the vast world of information gathering, it's essential to set clear objectives for your OSINT investigation. Some common use cases include:
- Cybersecurity Investigations: Identifying digital footprints, leaked data, and threat actors.
- Competitive Analysis: Gathering data on competitors for business intelligence.
- Background Checks: Verifying information about individuals or organizations.
- Social Media Monitoring: Tracking discussions and trends relevant to a topic or organization.
- Threat Intelligence: Identifying and assessing cyber threats such as phishing, fraud, and vulnerabilities.
Key Considerations:
- What specific information are you looking to find?
- What will you do with the information once you have it?

Step 2: Selecting the Right OSINT Tools
There are a variety of tools available to assist in OSINT investigations. Below are categories of popular tools for different types of investigations.
1. Search Engines
While general search engines (like Google) are useful, specialized search engines can yield more relevant results.
- Google Dorking: Using advanced search operators to filter results.
- Example:
site:example.com filetype:pdf confidentialcan help find specific types of documents.
- Example:
- DuckDuckGo: A privacy-focused search engine with no tracking.
2. Social Media Investigation Tools
- Social Searcher: Monitors and searches across social media platforms.
- Twint: An open-source Twitter scraping tool that can gather data without needing API credentials.
- IntelTechniques Social Media Search: An aggregation tool that allows you to search multiple social media platforms for user information.
3. Metadata and Document Analysis
- ExifTool: Extracts metadata from images and files, providing location, device information, and timestamps.
- FOCA (Fingerprinting Organizations with Collected Archives): Extracts metadata from documents to reveal sensitive information.
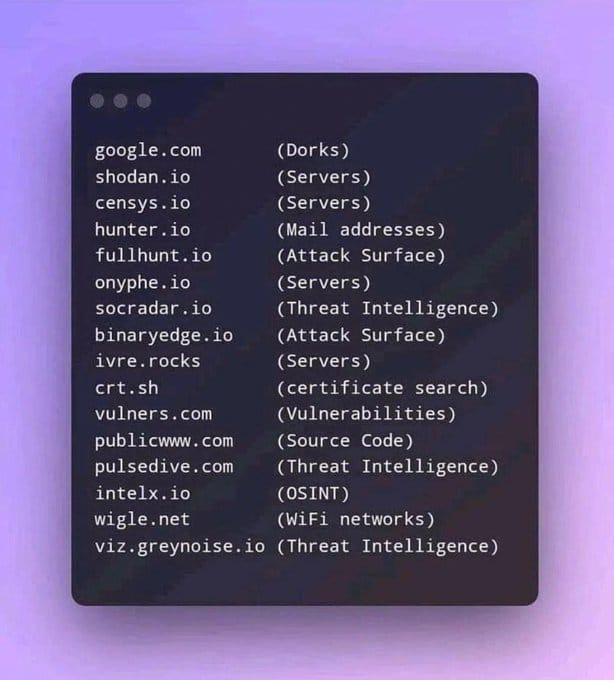
4. IP and Domain Analysis Tools
- DNSDumpster: Visualizes DNS information and subdomains of a website.
- Shodan: A search engine for discovering devices connected to the internet, such as routers, webcams, and IoT devices.
- WHOIS Lookup: Provides ownership information on domain names.
5. Public Records and Databases
- Pipl: A search engine for finding information about people.
- Have I Been Pwned: Checks if your email or domain has been part of a data breach.
- Public Registries: Many countries have open databases of corporate information, such as the UK's Companies House.
6. Networking and Network Traffic Analysis
- Wireshark: Captures and analyzes network traffic, useful for identifying potential leaks or security flaws.
- Censys: A search engine for discovering devices and networks exposed to the internet.
Step 3: Advanced Search Techniques
Using search engines effectively is crucial for OSINT investigations. Some of the advanced techniques you can employ are:
1. Google Dorking (Advanced Search Operators)
Google Dorking uses special search operators to refine search results:
site:example.com: Restricts results to a specific site.intitle:"index of": Searches for directory listings of websites.filetype:pdf confidential: Finds specific types of files.
Combine operators for more specific queries:
site:example.com inurl:admin filetype:xlsx confidential
2. Archived Content
Sometimes, content gets deleted or removed, but historical versions may still be accessible.
- Wayback Machine: An archive of websites that allows you to view previous versions of web pages.
- Google Cache: Find cached versions of a webpage by searching
cache:example.com.
3. Social Media Search Operators
Many social media platforms allow the use of search operators. For example, on Twitter:
from:username: Searches for tweets from a particular user.since:YYYY-MM-DD until:YYYY-MM-DD: Searches for tweets within a specific date range.
4. Reverse Image Search
- Google Reverse Image Search: Upload an image or paste a URL to find where else that image appears online.
- TinEye: Another reverse image search engine that also tracks the first appearance of an image online.
Step 4: Performing Reconnaissance on Individuals
1. Email Investigation
- Use Have I Been Pwned to check if an email is associated with any known breaches.
- Investigate email format patterns to derive potential emails for individuals in organizations.
2. Social Media Profiling
Tools like Twint (for Twitter) and Social Searcher can help gather social media activity.
- Look for patterns in posts, geolocation tags, and interactions to gain insights into the individual.
3. Username Analysis
- Many people use the same or similar usernames across multiple platforms. Use tools like Namechk to identify other accounts linked to a username.
4. Image and Location Data
If you're dealing with images, ExifTool can extract metadata, revealing geolocation, camera type, and timestamps.
Step 5: Legal and Ethical Considerations
OSINT relies on publicly available information, but it’s essential to navigate the legal and ethical boundaries. Unauthorized access, hacking, or the misuse of personal data can lead to legal consequences.
Key Guidelines:
- Always obtain data from publicly available sources.
- Be aware of data privacy laws, especially if dealing with sensitive or personal information.
- Verify the accuracy of the data you collect before taking any action based on it.
Step 6: Reporting and Analyzing OSINT Data
Once you've collected data, organizing it for analysis is crucial. Here’s how to ensure your findings are useful:
1. Data Organization
Use spreadsheets, databases, or tools like Maltego to visualize relationships between entities like IPs, domains, and social media accounts.
2. Data Validation
OSINT often involves sifting through large amounts of data, so cross-reference your findings with multiple sources to ensure accuracy.
3. Reporting
Create a clear and concise report outlining your findings, methodology, and any actionable intelligence. Use screenshots, metadata dumps, and document references to support your conclusions.
Step 7: Using OSINT for Cybersecurity
In cybersecurity, OSINT plays a vital role in threat intelligence, risk assessment, and proactive defense:
- Threat Intelligence: Monitor forums, dark web sites, and social media for potential threats or leaks. Tools like Shodan or Censys help identify vulnerable systems.
- Phishing and Fraud Detection: Identify phishing websites or fraudulent domains using DNSDumpster or WHOIS lookup.
- Reconnaissance in Penetration Testing: OSINT is often the first step in ethical hacking to gather valuable information about the target system or network before attempting an intrusion.
Conclusion
Open Source Intelligence (OSINT) is a powerful tool that can provide invaluable insights for cybersecurity professionals, investigators, and researchers. The process involves gathering, analyzing, and validating data from publicly available sources, leveraging both specialized tools and advanced search techniques. However, it's crucial to ensure that OSINT is used ethically and legally, respecting privacy laws and boundaries.