Advanced OSINT Techniques: From Basic Tools to Professional Intelligence Gathering

Open Source Intelligence (OSINT) has evolved into a cornerstone of modern intelligence operations, driven by technological advancements and the exponential growth of publicly available data. As we navigate 2025, OSINT practitioners must master a blend of traditional methodologies and cutting-edge tools to address complex challenges in cybersecurity, corporate intelligence, and threat detection. This guide explores advanced techniques, tools, and ethical frameworks shaping OSINT today.


Evolution of OSINT in 2025
The OSINT landscape in 2025 is defined by AI-driven automation, real-time analysis, and multimodal data integration. Key advancements include:
- AI and Machine Learning: Automated data collection, pattern recognition, and predictive analytics now enable analysts to process terabytes of data in seconds. Tools like OpenAI’s GPT models assist in text summarization and sentiment analysis, while platforms like Fivecast leverage AI for rapid threat detection[1][5][7].
- Real-Time OSINT: Critical for responding to dynamic events like cyberattacks or geopolitical crises. Social media feeds, satellite imagery, and dark web monitoring tools like Echosec Beacon and DarkOwl provide instantaneous insights[1][6][8].
- Multimodal Intelligence: Combining text, images, audio, and geospatial data into unified analysis frameworks. Meta’s Llama 3.3 exemplifies this trend, enabling cross-media query resolution[2].
- Smaller, Efficient Models: Open-source AI models like IBM Granite 3.1 prioritize energy efficiency and edge deployment, reducing reliance on cloud infrastructure[2][5].

Advanced Search Techniques and Operators
Mastering search operators is essential for precision in OSINT. Key strategies include:
1. Boolean Logic and Exact Matches
- Use
AND,OR, andNOTto refine queries (e.g.,"data breach" AND (LinkedIn OR Twitter)). - Enclose phrases in quotation marks for exact matches (e.g.,
"John Smith" CEO)[3].
2. Filetype and Site Operators
Narrow results to specific formats:
"confidential report" filetype:pdf site:example.com
This targets PDFs on a specific domain, ideal for corporate document retrieval[3][9].
3. Geolocation and Temporal Filters
- Use
before:2025-01-01orafter:2024-12-31to filter time-sensitive data. - Tools like Google Earth Engine enable geospatial analysis for disaster response or military operations[5][8].
Top Free Tools for 2025:
- Maltego (relationship mapping)
- Spiderfoot (automated reconnaissance)
- Google Dorking (advanced search syntax)[1][3]

Social Media Intelligence Gathering
Social media remains a goldmine for OSINT, but platforms like Snapchat pose unique challenges due to ephemeral content. Techniques include:
- Snapchat OSINT Workarounds:
- Use archival tools like Wayback Machine or Archive.today to capture public stories.
- Leverage username cross-referencing across platforms (e.g., searching a Snapchat handle on Instagram or Twitter)[3][5].
- Sentiment Analysis:
AI tools like Hugging Face transformers classify public sentiment toward brands or events[5][7].
Keyword and Hashtag Monitoring:
Tools like Social Searcher and Echosec track keywords, geotags, and trends across platforms. For example:
# Python script to scrape public tweets
import snscrape.modules.twitter as sntwitter
for tweet in sntwitter.TwitterSearchScraper('"data leak" since:2025-01-01').get_items():
print(tweet.content)

Dark Web OSINT Tools and Techniques
The dark web is a critical focus for threat intelligence. Key tools and methods include:
- Dark Web Crawlers:
- DarkOwl: Monitors darknet markets and forums for leaked credentials or ransomware discussions.
- Intelligence X: Archives historical data breaches and cryptocurrency transactions[4][5].
- Cryptocurrency Tracking:
Blockchain analysis tools like Chainalysis trace Bitcoin wallets linked to illicit activities[5]. - Automated Alerts:
Platforms like Recorded Future send real-time notifications for dark web mentions of critical assets[4].
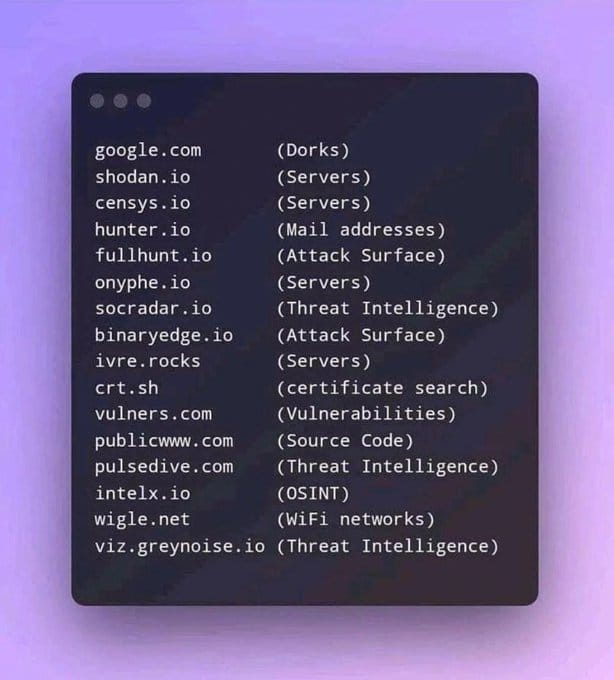
Corporate Intelligence Gathering
Businesses leverage OSINT for due diligence, competitor analysis, and compliance:
- Competitor Monitoring:
- SEMrush and SimilarWeb analyze web traffic and SEO strategies.
- LinkedIn Sales Navigator maps organizational hierarchies[5].
- Supply Chain Risks:
Satellite imagery tools like Sentinel Hub track shipping routes and port congestion[8]. - Brand Protection:
Tools like Talkwalker detect counterfeit products or trademark violations across e-commerce platforms[4].

OSINT for Threat Intelligence
Cybersecurity teams rely on OSINT to preempt attacks:
- Attack Surface Mapping:
Shodan identifies exposed IoT devices, while Censys scans for misconfigured servers[5]. - Phishing Detection:
Domain monitoring tools like PhishTank flag malicious sites impersonating legitimate brands[7]. - Ransomware Tracking:
Dark web crawlers identify ransomware group communications and decryptor releases[9].
Data Analysis and Visualization
Transforming raw data into actionable insights requires robust tools:
- Jupyter Notebooks:
Combine Python scripts with Markdown for reproducible analysis (e.g., pandas for data cleaning, matplotlib for visualization)[1]. - Tableau:
Create dashboards to map threat actor networks or corporate relationships[1]. - AI-Driven Clustering:
Unsupervised learning algorithms group similar data points (e.g., linking fake social media accounts)[2][7].
Privacy Considerations and Legal Frameworks
Ethical OSINT demands adherence to regulations like GDPR and CCPA:
- Compliance Tools:
Amass avoids scraping restricted content, while Osintracker logs data provenance for audits[1][9]. - Anonymization Techniques:
Use Tor or VPNs during investigations, and strip metadata from collected files[5][8]. - Legal Risks:
Avoid accessing password-protected sites or private social media profiles. The 2025 UK OSINT policy emphasizes proportionality in data collection[9].
Conclusion
The OSINT landscape of 2025 demands a balance of technical prowess and ethical rigor. By leveraging AI-enhanced tools, mastering advanced search operators, and adhering to legal frameworks, analysts can uncover critical insights while safeguarding privacy. As threats grow in sophistication, continuous learning and adaptation will remain the hallmarks of effective intelligence gathering.

Citations:
[1] https://www.osintguide.com/2024/11/14/osint-roadmap/
[2] https://www.ibm.com/think/news/2025-open-ai-trends
[3] https://publication.osintambition.org/osint-unleashed-top-10-search-operators-you-need-to-know-6283622e9d14
[4] https://www.talkwalker.com/blog/best-osint-tools
[5] https://digitaloneagency.com.au/osint-in-2025/
[6] https://www.einpresswire.com/article/782914175/global-open-source-intelligence-market-outlook-2025-2034-growth-drivers-share-and-trends
[7] https://www.fivecast.com/blog/osint-trends-for-2025/
[8] https://roke.co.uk/discover-the-latest-innovation-insights-roke/open-source-intelligence-trends-to-watch-for-in-2025
[9] https://blackdotsolutions.com/blog/this-year-in-osint-2025/
[10] https://www.talkwalker.com/blog/best-osint-tools
[11] https://hetheringtongroup.com/post/2025-osint-pathway
[12] https://incyber.org/en/article/2025-a-key-year-for-osint-and-cybersecurity/
[13] https://www.osintcombine.com/post/2025-the-changing-landscape-of-social-media-and-technology
[14] https://www.reddit.com/r/OSINT/comments/1i57zum/osint_in_2025/
[15] https://liferaftlabs.com/blog/osint-tools-security-analysts-should-know-for-2025
[16] https://duckalignment.academy/open-source-trends-2025/
[17] https://www.hstoday.us/subject-matter-areas/intelligence/evolution-of-osint-from-coup-crisis-to-cutting-edge-advancements-with-social-media-ai-and-data-analytics/
[18] https://www.sans.org/cyber-security-training-events/sans-osint-summit-2025/
[19] https://www.boxpiper.com/posts/osint-unlocking-the-power-of-intelligence
[20] https://www.linkedin.com/pulse/evolution-osint-beyond-modern-investigations-vub6f
[21] https://www.osinttechniques.com/advanced-search.html
[22] https://espysys.com/blog/10-advanced-osint-techniques/
[23] https://www.imperva.com/learn/application-security/open-source-intelligence-osint/
[24] https://www.webopedia.com/technology/9-free-osint-tools-for-2025/
[25] https://www.recordedfuture.com/threat-intelligence-101/tools-and-technologies/osint-tools
[26] https://github.com/The-Osint-Toolbox/OSINT-Advanced-Searching
[27] https://www.youtube.com/watch?v=aD-U2kP0vNk
[28] https://molfar.com/en/blog/how-to-find-information-on-anyone-the-best-osint-tools-for-people-search
[29] https://ethosrisk.com/blog/open-source-intelligence-advanced-search-tools/
[30] https://www.reddit.com/r/OSINT/comments/y0tafc/how_important_are_google_search_operators_google/
[31] https://www.recordedfuture.com/threat-intelligence-101/intelligence-sources-collection/social-media-threat-intelligence
[32] https://www.maltego.com/blog/everything-about-social-media-intelligence-socmint-and-investigations/
[33] https://medium.verylazytech.com/exploring-the-top-10-free-osint-tools-for-2025-5f23d0e4e49a
[34] https://www.aimtechnologies.co/social-media-monitoring-intelligence-the-power-of-digital-insights/
[35] https://github.com/osintambition/Social-Media-OSINT-Tools-Collection
[36] https://www.lexisnexis.com/en-int/glossary/media-intelligence/social-media-monitoring
[37] https://blog.hootsuite.com/osint-tools/
[38] https://www.zerofox.com/glossary/social-media-monitoring/
[39] https://www.youtube.com/watch?v=-zZkvaWFrs4
[40] https://flare.io/solutions/use-case/dark-web-monitoring/
[41] https://buddyxtheme.com/best-open-source-intelligence-osint-tool/
[42] https://www.zerofox.com/glossary/dark-web-threat-intelligence/
[43] https://www.zerofox.com/products/dark-web-monitoring/
[44] https://blackdotsolutions.com/blog/best-osint-tools/
[45] https://cybersixgill.com/dark-web-education-hub/dark-web
[46] https://www.crowdstrike.com/en-us/cybersecurity-101/threat-intelligence/dark-web-monitoring/
[47] https://github.com/apurvsinghgautam/dark-web-osint-tools
[48] https://slcyber.io
[49] https://www.csoonline.com/article/574585/10-dark-web-monitoring-tools.html
[50] https://www.niceactimize.com/fraud-management/dark-web-intelligence/
[51] https://salesfuel.com/open-source-intelligence-tools/
[52] https://www.aware-online.com/en/osint-tools/investigating-companies/
[53] https://www.rsaconference.com/library/blog/your-guide-to-osint-in-corporate-security
[54] https://www.neotas.com/osint-tools-and-techniques/
[55] https://osintacademy.com/foundations-of-osint-2025-cohort-3
[56] https://www.reddit.com/r/OSINT/comments/17a18o8/best_free_osint_tools_for_corporate_security/
[57] https://www.fivecast.com/blog/osint-trends-for-2025/
[58] https://blackdotsolutions.com/blog/open-source-intelligence-techniques/
[59] https://www.osint.industries
[60] https://www.sans.org/blog/what-is-open-source-intelligence/
[61] https://www.recordedfuture.com/blog/open-source-intelligence-definition
[62] https://osintteam.blog/top-osint-tools-for-cybersecurity-professionals-feac672efd39
[63] https://www.authentic8.com/resources/21-osint-research-tools-threat-intelligence
[64] https://www.csoonline.com/article/567859/what-is-osint-top-open-source-intelligence-tools.html
[65] https://www.babelstreet.com/solutions/osint-threat-intelligence-platform
[66] https://www.upguard.com/blog/open-source-intelligence
[67] https://www.ibm.com/think/topics/osint
[68] https://www.reddit.com/r/OSINT/comments/1d908nu/what_is_open_source_intelligence_to_you/
[69] https://www.neotas.com/osint-techniques/
[70] https://molfar.com/en/blog/top-osint-techniques
[71] https://www.newamerica.org/future-security/reports/preserving-privacy-an-impact-framework/exploring-the-intersection-of-osint-and-data-privacy-in-the-digital-world/
[72] https://www.recordedfuture.com/threat-intelligence-101/intelligence-sources-collection/osint-framework
[73] https://osintguide.com/2024/11/14/osint-roadmap/
[74] https://www.dhs.gov/sites/default/files/2022-09/Ethical Frameworks in OSINT Final.pdf
[75] https://eithos.eu/open-source-intelligence-osint-its-legal-and-ethical-aspects/
[76] https://molfar.com/en/blog/shcho-take-osint-u-2024-gaid-vid-molfar
[77] https://www.linkedin.com/pulse/privacy-vs-open-source-intelligence-osint-vijay-gupta--pidbc
[78] https://blogs.icrc.org/law-and-policy/2023/12/05/deploying-osint-in-armed-conflict-settings-law-ethics-theory-of-harm/
[79] https://www.tandfonline.com/doi/full/10.1080/08850607.2024.2387850
[80] https://proeliumlaw.com/open-source-intelligence-and-privacy/
[81] https://osinttraining.net/guide/an-introduction-to-search-engines/advanced-googleing/
[82] https://en.wikipedia.org/wiki/Social_media_intelligence
[83] https://brand24.com/blog/what-is-social-media-intelligence/
[84] https://www.osint.industries/post/social-media-intelligence-socmint-in-modern-investigations
[85] https://www.sprinklr.com/blog/social-media-intelligence/
[86] https://liferaftlabs.com/blog/7-best-osint-tools-for-social-media
[87] https://osintteam.blog/top-tools-that-will-change-osint-in-2025-a4d06c9212da
[88] https://www.osintteam.com/osint-tools-for-the-dark-web/
[89] https://www.maltego.com/blog/where-to-gather-intelligence-for-deep-dark-web-investigations/
[90] https://spycloud.com/use-case/dark-web-monitoring/
[91] https://osintteam.blog/top-open-source-intelligence-osint-tools-for-dark-web-bb9995bba489
[92] https://www.stealthmole.com/blog/beneath-the-surface-extracting-threat-intelligence-from-the-dark-web
[93] https://www.identityguard.com/news/dark-web-monitoring-services
[94] https://slcyber.io/government/
[95] https://sociallinks.io/industries/corporate-security
[96] https://www.osintguide.com/2024/11/14/osint-roadmap/
[97] https://www.crowdstrike.com/en-us/cybersecurity-101/threat-intelligence/open-source-intelligence-osint/
[98] https://www.globenewswire.com/news-release/2025/01/09/3007089/0/en/Open-Source-Intelligence-OSINT-Market-Poised-for-Explosive-Growth-of-USD-62-99-billion-by-2032-Driven-by-Cybersecurity-Demand-and-Advanced-Data-Analytics-Solutions-Research-By-SNS-.html
[99] https://linkurious.com/blog/20-osint-tools/
[100] https://flashpoint.io/intelligence-101/open-source-intelligence/
[101] https://www.zerofox.com/blog/how-open-source-intelligence-can-be-used-in-cyber-threat-hunting-zerofox/
[102] https://virtualcyberlabs.com/how-to-use-osint-for-cyber-investigations/
[103] https://www.wiz.io/academy/osint-tools
[104] https://www.cobalt.io/blog/top-osint-tools-techniques
[105] https://blackdotsolutions.com/blog/security-privacy-and-osint/
[106] https://cwsisecurity.com/what-is-open-source-intelligence-osint/
[107] https://digitaloneagency.com.au/osint-in-2025/
[108] https://petsymposium.org/popets/2023/popets-2023-0028.pdf
[109] https://corma-investigations.com/uncategorized/is-osint-legal-the-legal-and-ethical-concerns-of-using-open-source-intelligence/
[110] https://blackdotsolutions.com/blog/this-year-in-osint-2025/
[111] https://www.ukcybersecuritycouncil.org.uk/blogs/blogs/ethical-issues-of-osint/
[112] https://www.shrmonitor.org/assets/uploads/2023/05/article-Millett.pdf















